Table of Contents
Security Requirements Engineering
Among the research topics of the Security Group we focus on here on the design and validation of a methodology for security engineering that starts from the elicitation of socio-technical requirements down to the identification of security controls. Within the main stream project we covered a number of themes.
- Methodology for Early Requirements
- Compliance with Regulations
- Security under Evolution
Compliance with Regulations
The approach started from the Toronto i* goal modelling language which included the notions of goals and dependencies among actors. In the course of the project we refined it by introducing notion of actors’ relationship and goals focusing on permissions, entitlements, risks, and mitigation. With these concepts we could capture legal and compliance requirements, map them into a goal-based organizational model, and then refine it to a standard business process. A key issue in this respect is the ability to provide Compute Aided Support to decision makers, as the model in itself is not important: what we need is algorithms which take the model as input, distill the complexity of the model to bring new information to the human decision maker. If a construct doesn't bring a new algorithm, and the possibility for the decision maker to make a different decision, it is not worth adding it to the models.
The figure below from a multidisciplinary journal paper with SAP Researchers, and a law researcher on the integration of modeling for legal compliance describes how different stake-holders should interact with a level of details that is suitable for them. 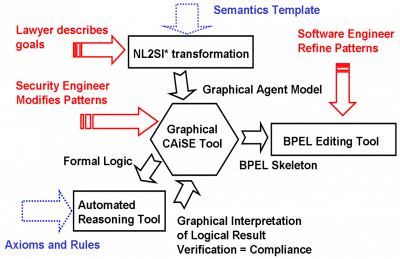
Evolving Security Requirements
Requirements evolution are unavoidable for any life-long system due to changes in business objectives, regulations, standards, environment or threats. In many cases, these changes are not completely unknown. For instance, the ongoing discussion in a standard body might feature two or three proposals, albeit might not be clear which one will finally win. A possible solution to the challenges of requirements evolution is to choose a good design alternative that could still work when evolution happens to minimize the risk and maximize the benefit.
While many approaches have been proposed to perform the management or consistency checking on requirements evolution, there has been less effort on delivering an explicit modeling and reasoning framework to assist decision managers select a good design alternative. We need to capture what Loucopoulous and Kavakli [ER-99] identified as the knowledge about “what the current state is”, “where the desired state to-be is in the future”, and “alternative designs” for the desired future state. In this respect it is important to provide a sound quantitative analysis, which is one of the current weaknesses identified by Dalal et al. [CACM-04] of many existing approaches.
We are working on a generic approach which tackles the fundamental issue of modeling and reasoning about requirements evolution to aid such decision making. The modeling support represents requirements evolution in terms of controllable and observable rules in which probability estimates can be accounted by using game-theoretic semantics. The reasoning support provides three quantitative metrics to identify which requirements must be implemented to guarantee the best chances of success (Max Belief) or minimize the risk of wasting money (Deferral Risk and Max Disbelief).
People
The following is a list of people that has been involved in the project at some point in time.
- Yudis Asnar
- Stephan Neuhaus
- Federica Paci
- Nicola Zannone
Projects
This activity was supported by a number of project
- SecureChange
- MASTER
- SERENITY
Publications
2013
- Tran L.M.S.: Early Dealing with Evolving Risks in Software Systems. In: The 3rd International Workshop on Information Systems Security Engineering (WISSE'13), co-located with CAiSE 2013, 17-21 June 2013, Valencia, Spain. PDF
2012
- Massacci F., Nagaraj D., Paci F., Tran L.M.S, Tedeschi, A. Assessing a Requirements Evolution Approach: Empirical Studies in the Air Traffic Management Domain. In Proceedings of International Workshop on Empirical Requirements Engineering (EmpiRE), 49–56, 2012.PDF.
- Paci F., Massacci F., Bouquet F., Debricon, S.Managing Evolution by Orchestrating Requirements and Testing Engineering Processes. In Proceedings of the Third International Workshop on Security Testing (SecTest), 834–841, 2012.PDF
2011
- Asnar, Y., Li, T., Massacci, F., Paci, F. Computer Aided Threat Identification. In Proceedings of the IEEE Conference on Commerce and Enterprise Computing (CEC), 145–52, 2011.PDF
- Felix, E., Delande, O., Massacci, F., Paci, F. Managing Changes with Legacy Security Engineering Processes.In Proceedings of the IEEE Intelligence and Security Informatics Conference (ISI), 137–142, 2011.PDF
- Bergmann, G., Massacci, F., Paci, F., Tun, T.T, Varro, D., Yu, Y. SeCMER: A Tool to Gain Control over Security Requirements Evolution.In Proceedings of ServiceWave, Demonstration Track, 49–56, 2011.PDF
- Bergmann, G., Massacci, F., Paci, F., Tun, T.T, Varro, D., Yu, Y. A Tool for ManagingEvolving Security Requirements. In Proceedings of CAISE'11 FORUM, 110–125, 2011.PDF
- Massacci, F., Mylopoulos, J., Paci, f.,Tun, T.T, Yu, Y. An extended Ontology for Security Requirements.In Proceedings of The First International Workshop on Information Systems Security Engineering (WISSE), 622–636, 2011.PDF
- F. Massacci and N. Zannone. Detecting Conflicts between Functional and Security Requirements with Secure Tropos: John Rusnak and the Allied Irish Bank. In Social Modeling for Requirements Engineering. MIT Press. A very interesting case study.PDF
- L.M.S.Tran and F.Massacci. Dealing with Known Unknowns: Towards a Game-Theoretic Foundation for Software Requirement Evolution. In Proceeding of the 23rd International Conference on Advanced Information Systems Engineering (CAiSE'11) London, June 2011.PDF
- L.M.S.Tran. Requirement Evolution: Towards a Methodology and Framework. In the CAiSE Doctoral Consortium 2011. London, June 2011. PDF
- Asnar Y., Massacci F., Saïdane A., Riccucci C., Felici M., Tedeschi A., El Khoury P., Li K., Seguran M., Zannone N.: Organizational Patterns for Security and Dependability: From Design to Application. International Journal of Secure Software Engineering 2(3):1-22 (2011)
Earlier papers
- Compagna L., El Khoury P., Massacci F., Saïdane A.: A Dynamic Security Framework for Ambient Intelligent Systems: A Smart-Home Based eHealth Application. Transactions on Computational Science 10:1-24 (2010)
- Compagna L., El Khoury P., Krausová A., Massacci F, and Zannone N..How to integrate legal requirements into a requirements engineering methodology for the development of security and privacy patterns. Artificial Intelligence and Law Journal 17(1):1-30, 2009.PDF
- Massacci F., and Mylopoulos J., Zannone N. Computer-aided Support for Secure Tropos. Automated Software Engineering. 14(3): 341-364, 2007 PDF. A comprehensive tutorial on the tool.
- Massacci F., Mylopoulos J., Zannone N., “From Hippocratic Databases to Secure Tropos: a Computer-Aided Re-Engineering Approach”. International Journal of Software engineering and Knowledge Engineering, 17(2):265-284, 2007.
- Y. Asnar, R. Bonato, P. Giorgini, F. Massacci, V. Meduri, C. Ricucci and A. Saidane. Secure and Dependable Patterns in Organizations: An Empirical Approach. In Proc. of IEEE RE'07, Industry Paper Track IEEE Press 2007
- F. Massacci, J. Mylopoulos and N. Zannone. Hierarchical Hippocratic Databases with Minimal Disclosure for Virtual Organizations. The VLDB Journal. 2006. PDF. AN application of the methodology based on goal model to extract schemas for hippocratic databases.
- Giorgini P., Massacci F., Mylopoulos J., Zannone N., “Requirements Engineering for Trust Management: Model, Methodology, and Reasoning”. International Journal of Information Security, 5(4):257-274, 2006. PDF. An introduction to the methodology.
- P. Giorgini, F. Massacci, J. Mylopoulos and N. Zannone. Detecting Conflicts of Interest. In Proc. of IEEE RE'06. pages 315-318. IEEE Press, 2006.
- Massacci F., Prest M., Zannone N., “Using a Security Requirements Engineering Methodology in Practice: the compliance with the Italian Data Protection Legislation”. Computer Standards & Interfaces, 2005, v. 27, n. 5, p. 445-455. PDF. One of our earliest papers and the most cited journal one.
- P. Giorgini, F. Massacci, J. Mylopoulos, N. Zannone: Modeling Security Requirements Through Ownership, Permission and Delegation. In Proc. of IEEE RE'05, IEEE Press 2005. (Ten Years Most Influential Paper IEEE RE 2015). PDF
- P. Giorgini, F. Massacci, J. Mylopoulos, N. Zannone: Modeling Social and Individual Trust in Requirements Engineering Methodologies. In Proc. of iTrust'05 LNCS Springer 2005. PDF
Talks and Tutorials
- Y. Asnar and Fabio Massacci. Managing Security in Services - a Goal & Process Approach. Tutorial at the IEEE International Conference on Intelligence and Security Informatics. 2011 Tutorial Material.
- Y. Asnar, H. W. Lim, F. Massacci, C. Worledge: Realizing Trustworthy Business Services by A New GRC. The ISACA Journal Online edition 2010. PDF
Software
- UNICORN : a tool for modeling and reasoning on the uncertainty of requirements evolutions. This is an Eclipse-based tool that aims to supports the modeling and reasoning on the uncertainty of requirements evolution. The tool provides graphical constructs as well as different views of requirements evolution to assist users to model requirements evolution. The reasoning facilitates the selection of design alternatives.
- A very old tool that we used in the first papers is here. http://sesa.dit.unitn.it/sistar_tool
