User Tools
This is an old revision of the document!
Table of Contents
Security Requirements Engineering
The main idea of this research activity is to design and validate a methodology for security engineering that starts from the elicitation of socio-technical requirements down to the identification of security controls.
The approach started from the Toronto i* goal modelling language which included the notions of goals and dependencies among actors. In the course of the project we refined it by introducing notion of actors’ relationship and goals focusing on permissions, entitlements, risks, and mitigation. With these concepts we could capture legal and compliance requirements, map them into a goal-based organizational model, and then refine it to a standard business process. A key issue in this respect is the ability to provide Compute Aided Support to decision makers, as the model in itself is not important: what we need is algorithms which take the model as input, distill the complexity of the model to bring new information to the human decision maker. If a construct doesn't bring a new algorithm, and the possibility for the decision maker to make a different decision, it is not worth adding it to the models.
The figure below from a multidisciplinary journal paper with SAP Researchers, and a law researcher on the integration of modeling for legal compliance describes how different stake-holders should interact with a level of details that is suitable for them. 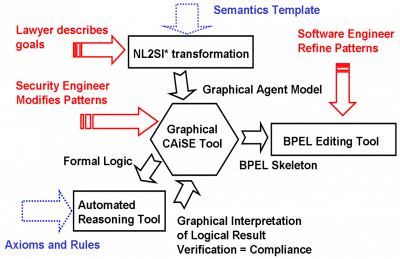
Themes
Within the main stream project we covered a number of themes.
- Security under Evolution
- Compliance with Regulations
- Methodology for Early Requirements
Projects
This activity was supported by a number of project
- SecureChange
- MASTER
- SERENITY
Publications
- Massacci F., Nagaraj D., Paci F., Tran L.M.S, Tedeschi, A. Assessing a Requirements Evolution Approach: Empirical Studies in the Air Traffic Management Domain. In Proceedings of International Workshop on Empirical Requirements Engineering (EmpiRE), 49–56, 2012.PDF.
- Paci F., Massacci F., Bouquet F., Debricon, S.Managing Evolution by Orchestrating Requirements and Testing Engineering Processes. In Proceedings of the Third International Workshop on Security Testing (SecTest), 834–841, 2012.PDF
- Asnar, Y., Li, T., Massacci, F., Paci, F. Computer Aided Threat Identification. In Proceedings of the IEEE Conference on Commerce and Enterprise Computing (CEC), 145–52, 2011.PDF
- Felix, E., Delande, O., Massacci, F., Paci, F. Managing Changes with Legacy Security Engineering Processes.In Proceedings of the IEEE Intelligence and Security Informatics Conference (ISI), 137–142, 2011.PDF
- Bergmann, G., Massacci, F., Paci, F., Tun, T.T, Varro, D., Yu, Y. SeCMER: A Tool to Gain Control over Security Requirements Evolution.In Proceedings of ServiceWave, Demonstration Track, 49–56, 2011.PDF
- Bergmann, G., Massacci, F., Paci, F., Tun, T.T, Varro, D., Yu, Y. A Tool for ManagingEvolving Security Requirements. In Proceedings of CAISE'11 FORUM, 110–125, 2011.PDF
- Massacci, F., Mylopoulos, J., Paci, f.,Tun, T.T, Yu, Y. An extended Ontology for Security Requirements.In Proceedings of The First International Workshop on Information Systems Security Engineering (WISSE), 622–636, 2011.PDF
- Asnar Y., Massacci F., Saïdane A., Riccucci C., Felici M., Tedeschi A., El Khoury P., Li K., Seguran M., Zannone N.: Organizational Patterns for Security and Dependability: From Design to Application. International Journal of Secure Software Engineering 2(3):1-22 (2011)
- Compagna L., El Khoury P., Massacci F., Saïdane A.: A Dynamic Security Framework for Ambient Intelligent Systems: A Smart-Home Based eHealth Application. Transactions on Computational Science 10:1-24 (2010)
- Compagna L., El Khoury P., Krausová A., Massacci F, and Zannone N..How to integrate legal requirements into a requirements engineering methodology for the development of security and privacy patterns. Artificial Intelligence and Law Journal 17(1):1-30, 2009.
- Massacci F., and Mylopoulos J., Zannone N. Computer-aided Support for Secure Tropos. Automated Software Engineering. 14(3): 341-364, 2007
- Massacci F., Mylopoulos J., Zannone N., “From Hippocratic Databases to Secure Tropos: a Computer-Aided Re-Engineering Approach”. International Journal of Software engineering and Knowledge Engineering, 17(2):265-284, 2007.
- Giorgini P., Massacci F., Mylopoulos J., Zannone N., “Requirements Engineering for Trust Management: Model, Methodology, and Reasoning”. International Journal of Information Security, 5(4):257-274, 2006.
- Massacci F., Prest M., Zannone N., “Using a Security Requirements Engineering Methodology in Practice: the compliance with the Italian Data Protection Legislation”. Computer Standards & Interfaces, 2005, v. 27, n. 5, p. 445-455.
Talks and Tutorials
- Y. Asnar and Fabio Massacci. Managing Security in Services - a Goal & Process Approach. Tutorial at the IEEE International Conference on Intelligence and Security Informatics. 2011 Tutorial Material.
