User Tools
This is an old revision of the document!
Table of Contents
Securing Access to Cloud Storage
Data outsourcing is a growing business model offering services to individuals and enterprises for processing and storing a huge amount of data. It is not only economical but also promises higher availability, scalability, and more effective quality of service than in-house solutions. Despite all its benefits, data outsourcing raises serious security concerns for preserving data confidentiality. Not only data but policies, regulating access on data, may reveal sensitive information when they are available in cleartext on the cloud. Therefore, the major research challenges include protection of data, as well as access control policies.
The Proposed Approach
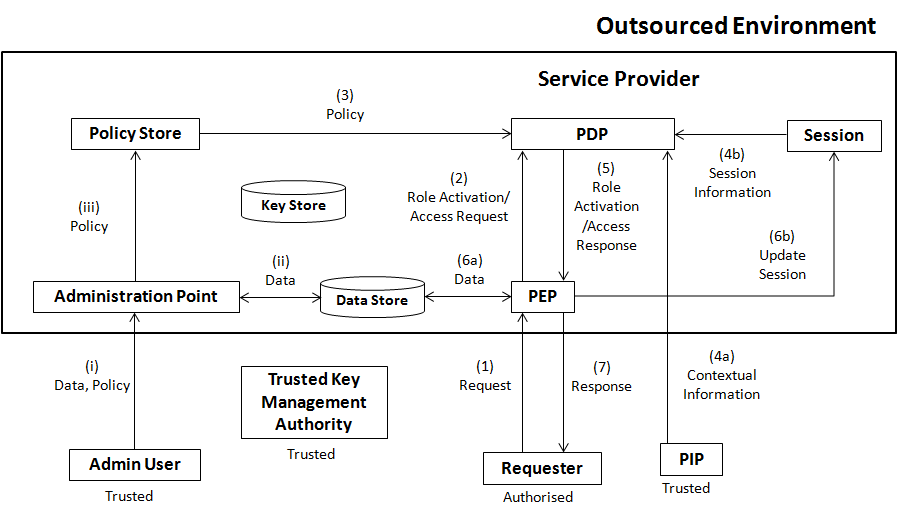
The proposed architecture aims at providing mechanism that can be deployed in an outsourced environment. The following figure illustrates the proposed architecture that has similar components to the widely accepted architecture for the policy-based management proposed by IETF. The proposed architecture uses proxy re-encryption to protect data and access control policies, where a Trusted Key Management Authority (TKMA) distributes keys to users including Admin User and Requester. The TKMA sends server side keys to the Key Store managed by the Service Provider in the Outsourced Environment. In the proposed architecture, an Admin User deploys (i) encrypted data and policies (that regulate access on data) and sends them to the Administration Point that re-encrypts and stores (ii) data and (iii) policies in the Data Store and the Policy Store, respectively. A Requester may send (1) the request to the Policy Enforcement Point (PEP). The PEP forwards (2) the role activation or the access request to the Policy Decision Point (PDP). After receiving the request, the PDP first retrieves (3) Policies from the Policy Store. Optionally, PDP fetches (4a) Contextual Information and (4b) Session Information from Session and the Policy Information Point (PIP), respectively. After making the decision, the PDP sends response to the PEP. The PEP provides access to the data (6a) and updates session (6b). Finally, a response is sent to the Request (7).
Themes
Among the research topics of the Security Group, the main stream of this research topic is to regulate access to cloud storage without leaking private information about the sensitive data. In this research activity, we covered a number of themes, in particular,
- Querying encrypted data securely
- Enforcement of encrypted security policies
- Enforcing Role-Based Access Control (RBAC) in an encrypted manner
- Secure enforcement of dynamic security constraints
People
The following is a list a people that have been involved in this research activity at some point in time.
- Muhammad Rizwan Asghar (active)
- Mihaela Ion
- Giovanni Russello (active)
- Bruno Crispo (active)
Publications
- Muhammad Rizwan Asghar, Mihaela Ion, Giovanni Russello, and Bruno Crispo, ESPOONERBAC: Enforcing security policies in outsourced environments, Elsevier Computers & Security (COSE), 2012. In Press. PDF
- Mihaela Ion, Giovanni Russello, and Bruno Crispo, Enforcing Multi-user Access Policies to Encrypted Cloud Databases, In Proceedings of the 12th IEEE International Symposium on Policies for Distributed Systems and Networks (POLICY), Pisa, Italy, June 2011.
- Muhammad Rizwan Asghar, Giovanni Russello, and Bruno Crispo, Poster: ESPOONERBAC: Enforcing security policies in outsourced environments with encrypted RBAC, In Proceedings of the 18th ACM Conference on Computer and Communications Security, CCS '11, pages 841-844. ACM, 2011.
- Muhammad Rizwan Asghar, Mihaela Ion, Giovanni Russello, and Bruno Crispo, ESPOON: Enforcing Encrypted Security Policies in Outsourced Environments, In Proceedings of the 6th International Conference on Availability, Reliability and Security, ARES'11, pages 99-108. IEEE Computer Society, August 2011. PDF
- Muhammad Rizwan Asghar, Mihaela Ion, Giovanni Russello, and Bruno Crispo, Securing Data Provenance in the Cloud, IFIP WG 11.4 - Open Problems in Network Security (iNetSec), Lucerne, Switzerland, June 2011. PDF
Talks, Tutorials and Demo
- Muhammad Rizwan Asghar, ESPOON: Enforcing Security Policies in Outsourced Environments, SRI International, Menlo Park, California, USA, August 2012. Slides
- Muhammad Rizwan Asghar, Enforcing Security Policies in Outsourced Environments, The 3rd Workshop on Cryptography (BunnyTN3), Trento, Italy, March 2012.
- Muhammad Rizwan Asghar, ESPOON: Enforcing Encrypted Security Policies in Outsourced Environments, The 6th IEEE International Conference on Availability, Reliability and Security (ARES), Vienna, Austria, August 2011.
- Muhammad Rizwan Asghar, Securing Data Provenance in the Cloud, IFIP WG 11.4 - Open Problems in Network Security (iNetSec), Lucerne, Switzerland, June 2011.
- Muhammad Rizwan Asghar, Enforcing Multi-user Access Policies to Encrypted Cloud Databases, The 12th IEEE International Symposium on Policies for Distributed Systems and Networks (POLICY), Pisa, Italy, June 2011.
Projects
Software
- We have developed a prototype for securing data, as well as access control policies in outsourced environments. To get the source code, please contact Muhammad Rizwan Asghar.