User Tools
This is an old revision of the document!
Table of Contents
DETERLab
Requirements
This exercise requires basic OS and networking knowledge, understanding of Denial of Service (DoS) and buffer overflows. It also involves coding skills. It can be done in introductory and advanced security classes.
Setup
Before the exercise you need to perform the following steps:
- Create groups of students in your class project on DETERLab, one group per attack team.
- Swap in the experiment using the related NS file:
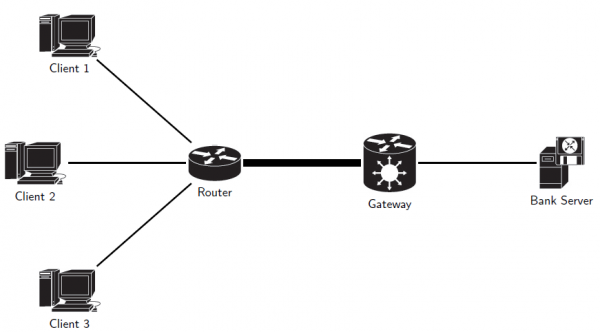
/share/education/CTF2_USC/ctf2.ns
. The obtained topology is described in the following picture.
 Swap in as many experiments as you have teams. Give to the groups easily related names, e.g., “cctf-team1” since managing multiple copies of experiment and multiple teams could easily get confusing.
Swap in as many experiments as you have teams. Give to the groups easily related names, e.g., “cctf-team1” since managing multiple copies of experiment and multiple teams could easily get confusing.
- In each experiment, remove access to the three client machines for all but their attack team, and remove access to server and gateway machine for all but the automated defense team. Remove also the access to router for all teams. These steps can be done by running the setexpgroups.sh script:
$ ./setexpgroups.sh ProjName expgroups mysql
where
mysqlis the configuration of the bank service offered by the server, whereasexpgroupsis a text file which specifies, by means of its two lines, the names of the experiments and the associated group names. An example theexpgroupsfile is shown down here.exp1 exp2 exp1-attack-group exp1-defense-group exp2-attack-group exp2-defense-group
This step will ensure that during exercise team members cannot log into machines controlled by the opposing team and spy on them.
cd ciao
